This article is reprinted from MainTest233's column article on Zhihu https://zhuanlan.zhihu.com/p/675492255, with permission obtained. Please follow the CC BY-NC-SA agreement when reprinting.
Some notes regarding this article on the Zhihu platform:
Since this article was originally published on V2EX, but some users on that platform cannot access it, it has been reprinted to Zhihu.
Zhihu may not recognize some Markdown syntax, so some formatting may appear abnormal; please forgive this.
The original text used a GitHub repository as an image host, which some domestic users may not be able to access. Therefore, I have mirrored most of the images in this article. If any images are missing, please let me know in the comments, and I will promptly replace the mirror links.
Hello everyone, this is MainTest233, a former spokesperson for HiPer during related events.
I believe most of you have not forgotten this incident from a year ago.
PS: If you have forgotten or do not know what this matter is, you can take a look at these articles:
- BakaXL's Response to Recent Related Articles
- Joint Announcement on the Next Development of PCL2 / HMCL / BakaXL's Multiplayer Function
- Why Did MC Launchers Shut Down Multiplayer Functions? What Hidden Secrets Are Behind It?
- When the Open Source Community Encounters Commercial Companies That Openly Violate Open Source Agreements, What Can We Do Besides Feeling Helpless?
I apologize for bringing up this very troubling matter at the end of the year, but we have to mention it today.
Through some rumors, I learned that HiPer has recently successfully rebranded and is preparing to make a comeback.
Although I am no longer involved in the Minecraft community, for certain reasons, I feel it is necessary to make some insignificant compensations for what I did in the past. I will disclose some superficial information I learned while in the HiPer joint development group and use this to provide a warning to everyone, to a certain extent, to curb HiPer's resurgence (Of course, I also know that the cat will not give up because of this; after all, haters are also traffic)
In this article, I have tried to beautify the text using Markdown syntax as much as possible and have made multiple checks and modifications to correct the previous chaotic formatting and illogical issues.
Please set aside your irritations and patiently read this article to the end.
Please note that I have personally withdrawn from HiPer-related matters and no longer participate in any launcher-related activities. Therefore, this article does not represent any position; it is merely a summary of my personal concerns regarding recent situations.
Since previous articles by various launcher authors have provided a comprehensive summary of past events, and since I no longer have complete evidence regarding previous matters, I will only discuss recent new events here.
Cause#
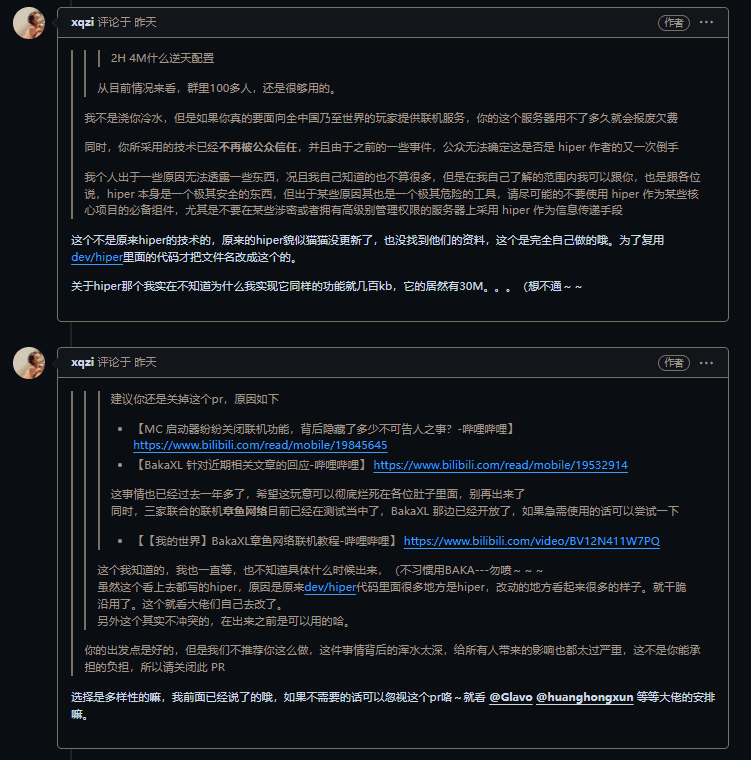
On December 29, 2023, at 11:24 PM, a GitHub user named xqzi submitted an Issue in the official open-source repository of HMCL. The content simply summarized that this xqzi had imitated HiPer to create a similar tool and had purchased a 2C?G4M Alibaba Cloud server to replace HiPer's relay server.
But to be honest, I’m not mocking you; at that time, HiPer mainly relied on the backbone line servers of its enterprise product Matrix. We were using an 8C16G12M Tencent Cloud relay node that was not even connected to the backbone network and was almost overwhelmed. Your small server trying to support a tool that could potentially have hundreds of thousands of users during holidays is truly overestimating its capabilities.
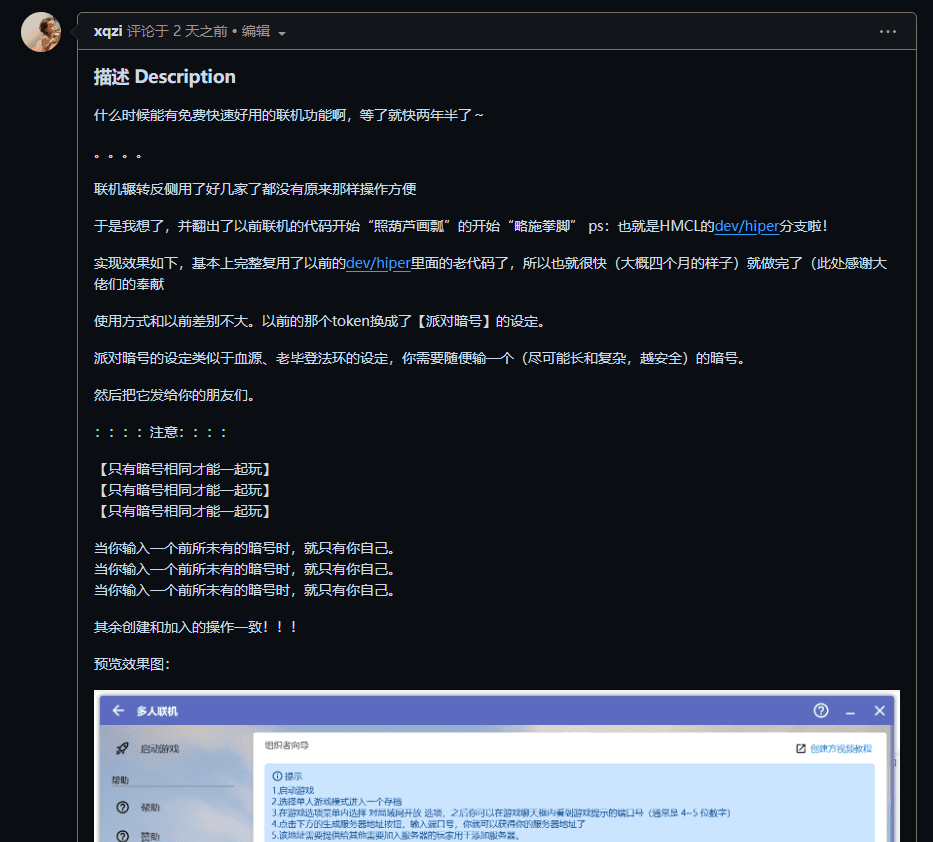
Knowing how deeply HiPer had impacted developers and users before, I did not want this matter to resurface in public. Given that the resources provided by this person were indeed too scarce, I suggested that they refrain from trying to pursue this further, but clearly, I failed.
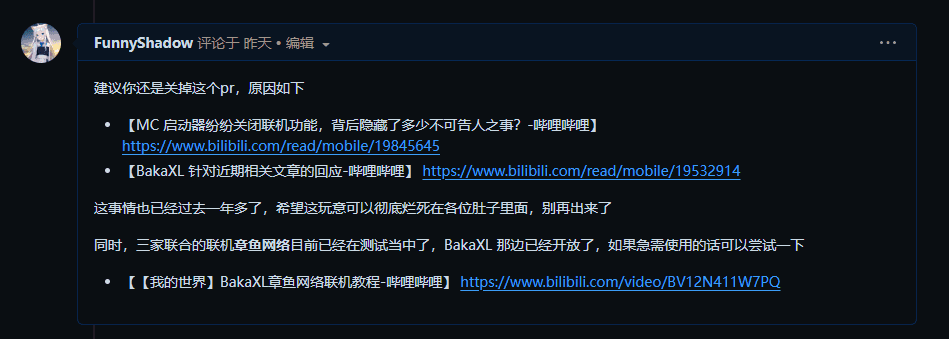
At this point, the issue was not very serious. Soon, a code contributor from HMCL, burningtnt, noticed this Issue and contacted someone with the authority to manage Issues. We just needed to wait for the repository administrator to come and lock the Issue and give a final reply, and this matter would be over.
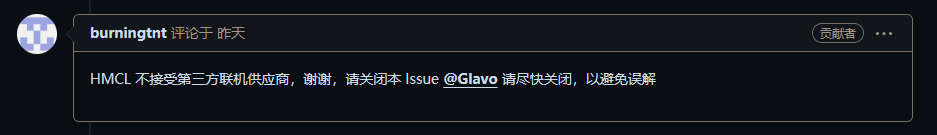
But at this moment, someone who caused all this appeared.
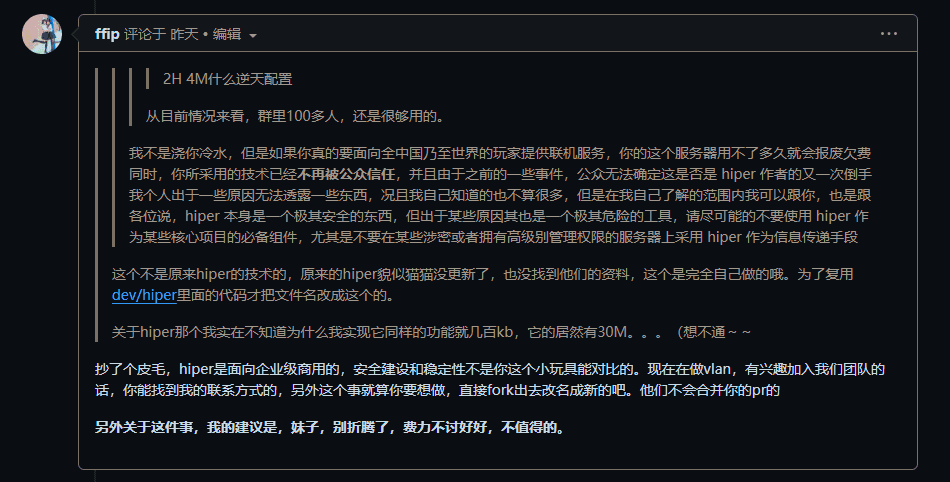
A familiar tone, a suggestive avatar, a short name, it's him, it's him, it's him, our cat.
Let me introduce this ffip, who is the author of HiPer, Cat.
From this point on, the entire Issue began to develop in an uncontrollable direction.
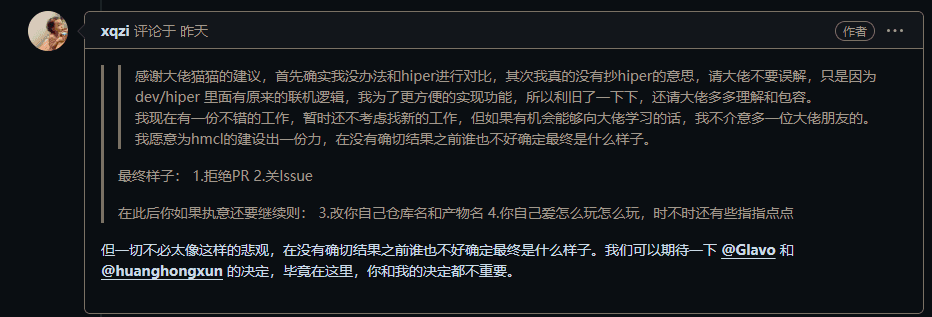
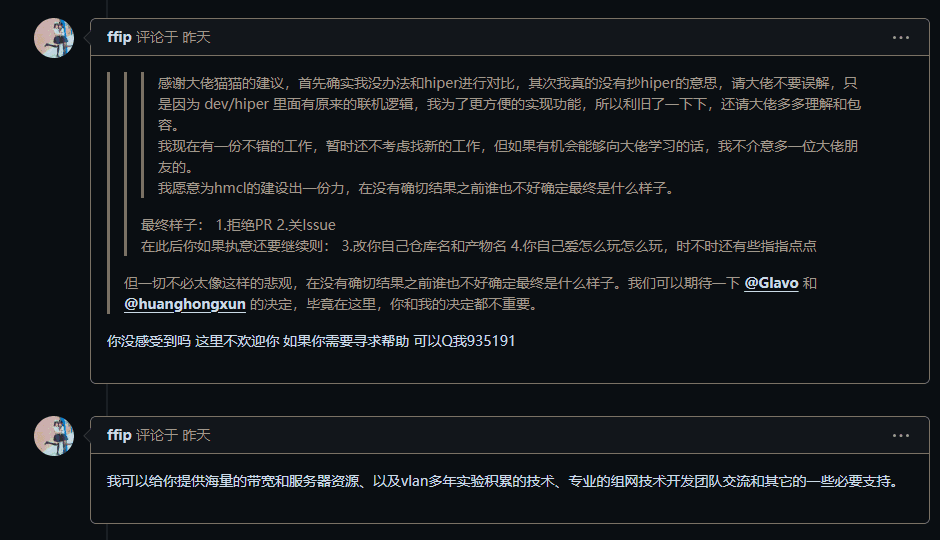
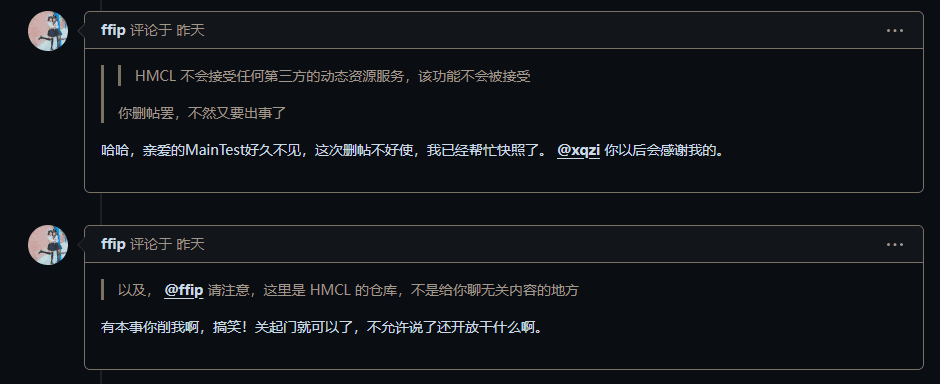
Familiar words evoke unpleasant memories. It is clear that Cat is preparing to use his seductive tactics to deceive a pawn, using them to complete HiPer's comeback while also throwing in a few jabs.
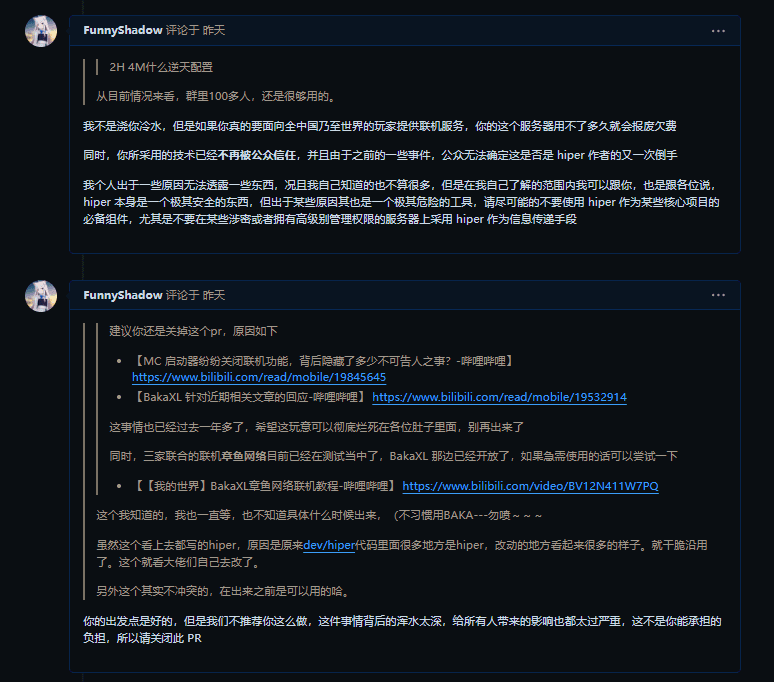
But I cannot understand how deceiving a still-unfinished high school student is something that can be done with a clear conscience. After all, I have no burdens; even if I abandon it, I have no ability to affect your subsequent business.
But this is a middle-aged person who already has a job. The aforementioned xqzi indeed mentioned that if discovered while doing private work, it would lead to serious consequences. Your current behavior is nothing less than leading them astray and potentially ruining their life.
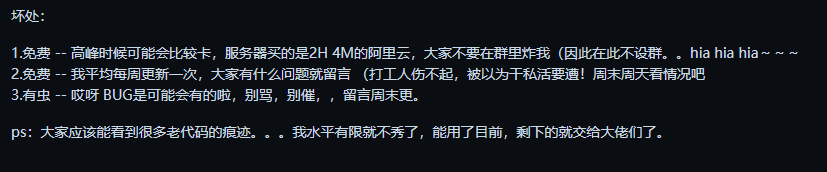
Since I have not yet completed my studies, I cannot fully understand the pressures and burdens of middle-aged people. However, from my personal family perspective, if my parents suddenly lost their jobs, the consequences would be a complete breakdown of the family. This is no longer a simple matter of using others as pawns or stepping stones for one's own benefit.
But clearly, Cat has not given up on this opportunity for HiPer to make a comeback. After all, for him, nothing is more important than his own interests.

By the way, your project name is also a duplicate, and it's a project from 6 years ago.

Thus, I can no longer continue as a bystander enjoying the spectacle.
But as mentioned earlier, I do not have any powerful abilities to counter HiPer; however, I have something that HiPer has never disclosed to the public, and now it is time for it to make its appearance.
Here’s a small aside: due to some unexpected events, I leaked information to a group chat where a certain insider of Cat is located before publishing this article. Currently, Cat has publicly shared this configuration with everyone (I will provide it later), but I can tell you that this thing still poses a significant security risk. Please continue reading for details.
Strange Port#
Here’s another aside: after another rebranding, HiPer has now been renamed to VLAN.
In fact, this issue is quite simple and not particularly huge.
I wonder if you have noticed that HiPer creates a very strange listener when it starts.
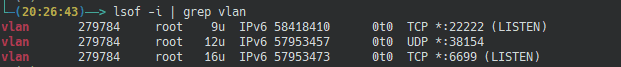
As shown in the image, 38154 (UDP) is a port dedicated to STUN, while 6699 (TCP) is used for P2P connections.
(PS: At this time, I just roughly scanned with nmap and did not use WireShark for detailed packet capturing; I just relied on memory. You just need to know that these two ports are normal.)
But there is a very strange 22222 (TCP) port in the image. What is it used for?
Since lsof and netstat cannot identify the function of this port, let’s use nmap to perform a quick scan on this port to see.
 .
.
I was shocked when I looked at it; I thought I had misconfigured some SSH port!
However, this fingerprint-strings also proves that this is indeed HiPer's doing, and it even carries an SSH public key pair that I have never seen before. For this reason, I specifically checked my SSH public key file and found that there was nothing there.

For this reason, I once asked Cat what this was. Cat called it "edge control." How should I put it? This naming method can only be attributed to Cat~~ (Of course, I no longer have screenshots of that chat record; feel free to criticize me for spreading rumors)~~
Trust me, don’t search for what edge control is, or you will have the same mind-blowing feeling as I did.
In simple terms, according to what Cat told me at the time, this SSH is a "backup plan." When certain users violate the ToS or even break the law, Cat can use this to collect relevant evidence for law enforcement.
If this thing is really applied to law enforcement, it would indeed be a great thing, but, is it true?
Open Portal#
You didn’t think this was the end, did you? Far from it.
I once naively thought that this thing could only be accessed by the central control server, but imagine if this network is not isolated?

At this point, I must apologize to TT702 for my previous stubbornness and rudeness, and I offer my sincerest respect. His previous views on HiPer were thoroughly validated at this moment.
HiPer's edge control feature does not perform any additional authentication; it only requires joining the network and possessing a correct private key to access any device on the network that has not configured a firewall.
You might think, "Ah, this thing can just be blocked by turning on the firewall, right?" The fact is indeed so, but what if I tell you that most household devices in China do not have firewalls enabled? What if they automatically request firewall permissions but do not inform you what this thing is for? And when a novice wants to use this tool for multiplayer, or someone who doesn’t understand much wants to use it to set up a network, when they are blocked by the firewall, will they choose to seriously ponder the firewall rules or simply turn off the firewall?
You might think, "This thing is just an SSH; it doesn’t have any permissions. What can it do?" Then I can use another simple experiment to tell you why this thing is so dangerous.


As shown, I created a test account without permissions and tried to rerun HiPer. You can clearly see that HiPer must be run with administrator privileges to perform certain operations. This is not difficult to understand because it is almost impossible to implement network forwarding using TUN without administrator privileges. This means that I currently have a SSH service running on my server with administrator privileges that can be accessed by anyone with the SSH key file.
If you cannot understand this, let me give you a simple example: it’s like you leave your front door wide open and display all your valuables outside.
Moreover, this feature does not have a shutdown method provided in the official tutorial, and my configuration does not enable this feature.

According to the official tutorial of HiPer, I can indeed change the port of this service and replace the key with my own by adding the ssh section, but I still cannot completely disable this feature. Once I delete this section, SSH will restore to the public key with that SSH public key; moreover, this feature must delete the sync section shown in the image, which mainly synchronizes the point.yml above with the same content in the official repository. This part is your main relay node connecting to the entire network and will be updated dynamically at regular intervals. If you do not delete this part, any modifications you make will be reset. If you delete it, you will lose the permission to update the relay node that ensures your stable and fast connection to the entire network. What a dilemma!
(Oh, and if there hadn’t been a leak in advance, I’m afraid this ssh section prompt wouldn’t have appeared by now.)
Moreover, this feature already existed when the three launchers were opposed to HiPer and had not completely removed HiPer.
Furthermore, looking further back, I see that the former official forum of HiPer mcer.cn now has some government-related content. It is evident that Cat has prepared or may have already pushed HiPer's business into the BG sector. I think no enterprise or government would want such a serious backdoor left in the networking tools they use.
At one point, during a conversation, Cat mentioned this matter to me, and he expressed the possibility of using this to gain an overwhelming advantage. Whether it is true, no one knows; perhaps only Cat knows in his heart.
Epilogue#
This article is basically coming to an end. I have tried to submit this issue to the official CVE platform and CNNVD (although the likelihood of this being recorded is almost zero; just consider it for fun).
After reading this article, I believe you have a new understanding of HiPer.
Although the content disclosed in this article is not severe, please be cautious of HiPer and its author Cat. This may very well be just the tip of the iceberg.
Regarding the current situation, I have little advice to offer, as my knowledge is quite limited.
- Use Cat's works less.
- Enable firewalls and scrutinize each one.
- Implement proper permission controls; do not casually grant software administrator privileges.
I have said all I needed to say. If you want to criticize me, feel free to express your thoughts in the comments below this post. I will not delete any comments, and I won’t mind personal attacks against me, after all, haters are also traffic.
Oh, and if this post gets deleted, I will continue to post. If it doesn’t work, we can switch platforms. We can see who has more reports or accounts.
Of course, you can also use some financial power to directly ban me across all platforms, but in that case, everyone will understand who is black and who is white.
The views in this article are for everyone to judge; I merely describe the facts objectively. If you think I might be fabricating or spreading rumors, feel free to comment below my article to let me know.
I tested using the VLAN (1.15.1.0) version of Linux_x86-64, and both servers are running Debian 12 (Bookworm). I will keep this binary file and have made off-site multi-center backups. If you want, you can break into ED25519, OneDrive, Synology NAS, LUKS, etc., and trace back to my personal address to find the last file I hid and delete this content. However, I think you probably won’t care, as this is just a small piece of information.
Oh, by the way, don’t you like Wayback Machine? At the time of writing this article, I took snapshots of the main usage tutorial and repository homepage for you. Although I couldn’t capture the time when you didn’t write the SSH configuration, I’m curious how many configurations you will open up that you didn’t write down afterward, and I’m also curious how many changes you will make in response to the questions I raised above. Let’s wait and see.
If you don’t believe it, you can check the repository’s commit history; it has been updated to version 1.15.1.0, but there are only 2 commits in the repository. The number of git pull and git push that went through is worth pondering.
Relevant links:
- Official tutorial: https://docs.qq.com/aio/DTEpsR1lmbnZLQmln?p=gbkSEKVrKc6kV7qa6SLZ0y
WayBack Machine: https://web.archive.org/web/20231231141501/https://docs.qq.com/web/20231231141501/https://docs.qq.com/aio/DTEpsR1lmbnZLQmln?p=gbkSEKVrKc6kV7qa6SLZ0y - Official binary file repository: https://gitcode.net/to/vlan
WayBack Machine: https://web.archive.org/web/20231231142556/https://gitcode.net/to/vlan - Official binary file repository commit page: https://gitcode.net/to/vlan/-/commits/master/
WayBack Machine: https://web.archive.org/web/20231231142645/https://gitcode.net/to/vlan/-/commits/master/ - CVE introduction Gist: https://gist.github.com/FunnyShadow/ba8177d50f146034b47de296e514f5de
By the way, there is actually a solution: you can pay Cat to get a customized version of the HiPer interconnection tool that does not require administrator privileges. What do you think?

Finally, xqzi hopes I give you a response to understand the truth behind why I stopped you from participating in this matter. This is the reason, and it’s not just this.
“What can be said is not pain.”
In the last sentence, all images in this article come from personal repositories on GitHub. Therefore, when the content in the GitHub repository is modified, this will also be dynamically updated here.
To show my sincerity, I have also processed the commits of the image storage repository through WayBack Machine. Here are the links:
- Image repository commit page: https://github.com/FunnyShadow/some-backups-of-hiper/commits/main/
WayBack Machine: https://web.archive.org/web/20231231143949/https://github.com/FunnyShadow/some-backups-of-hiper/commits/main/
This article is archived and will not be modified further.